Getting familiar with Application Security
Getting familiar with Application Security
Now that Application Security is enabled, lets explore the product and analyze some vulnerabilities.
Vulnerabilities
On this screen you can see a list of all vulnerabilities that were discovered in the environment.
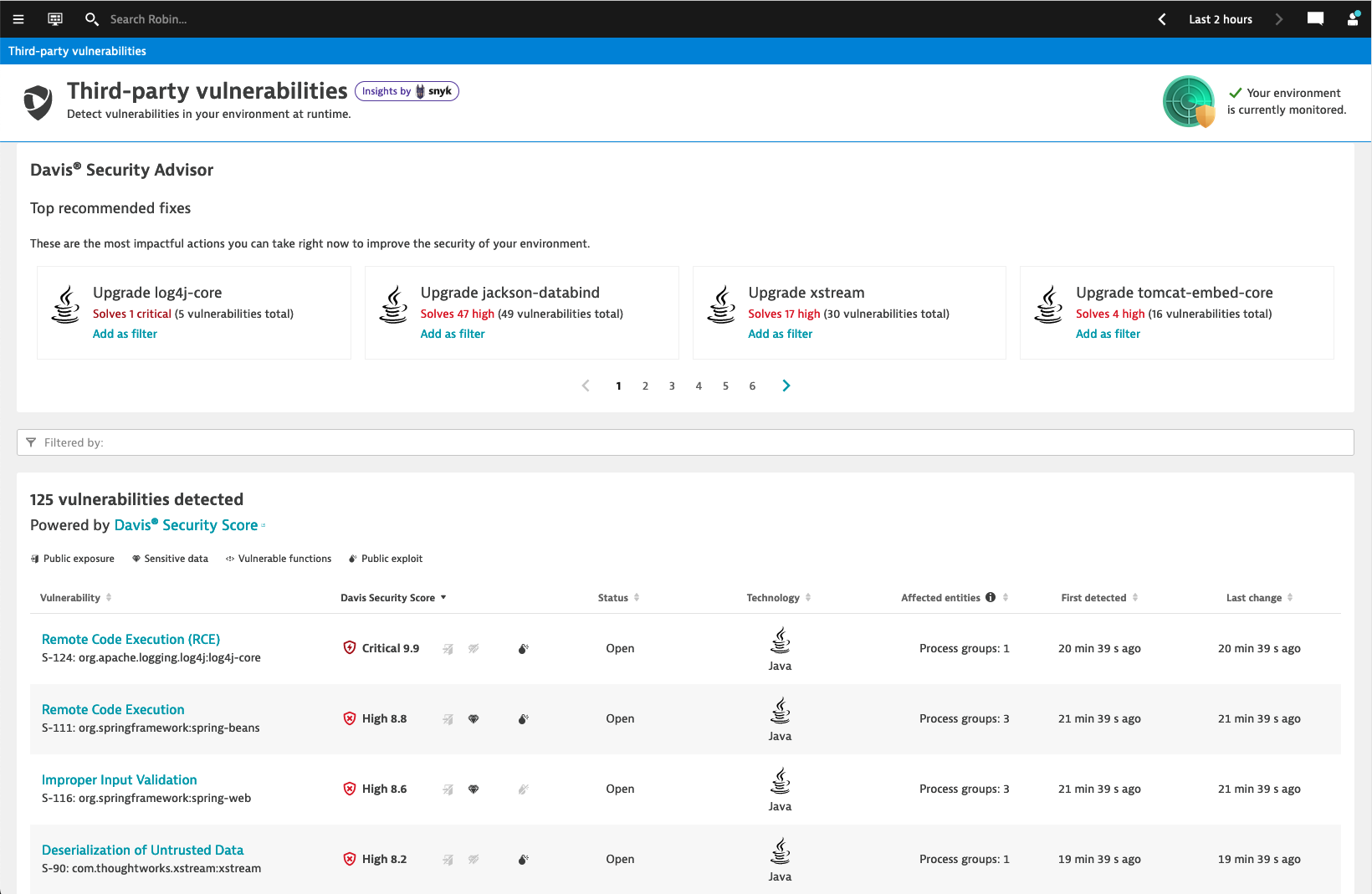
The list is sorted by the Davis Security Score, which is based on the CVSS, but also factors in context information detected at runtime. This contextual information, shown as icons next to the Davis Security Score, indicates whether there is public exposure, sensitive data in range, presence of vulnerable functions, and availability of a public exploit.
📓 Contexual Information
- Public exposure: The vulnerability affects a process that is exposed to the internet, based on the Dynatrace entity model (Smartscape).
- Sensitive Data: The vulnerability affects a process that has database access, based on the Dynatrace entity model.
- Vulnerable Functions: The vulnerable code of the affected librariy is actively used. We have not enabled this yet, therefore this information won’t be displayed.
- Public Exploit: There is a known exploit for this vulnerability.
Tasks to complete this step
📓 In March 2022 a critical vulnerability was discovered in the Spring Framework. The affected versions of the Spring Beans library are vulnerable to Remote Code Execution (RCE), allowing attackers to install a web shell on a victim’s application by manipulating the classloader with a specific HTTP Post request.
Let’s see if we are affected by this vulnerability.
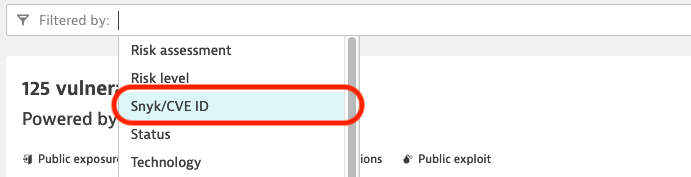
- Click on the Filter by field, select Snyk/CVE ID and enter CVE-2022-22965.
 As you can the vulnerability was detected in your environment, with a Davis Security Score of 8.8 out of 10. It also shows you that there are 3 process groups that are affected.
As you can the vulnerability was detected in your environment, with a Davis Security Score of 8.8 out of 10. It also shows you that there are 3 process groups that are affected. 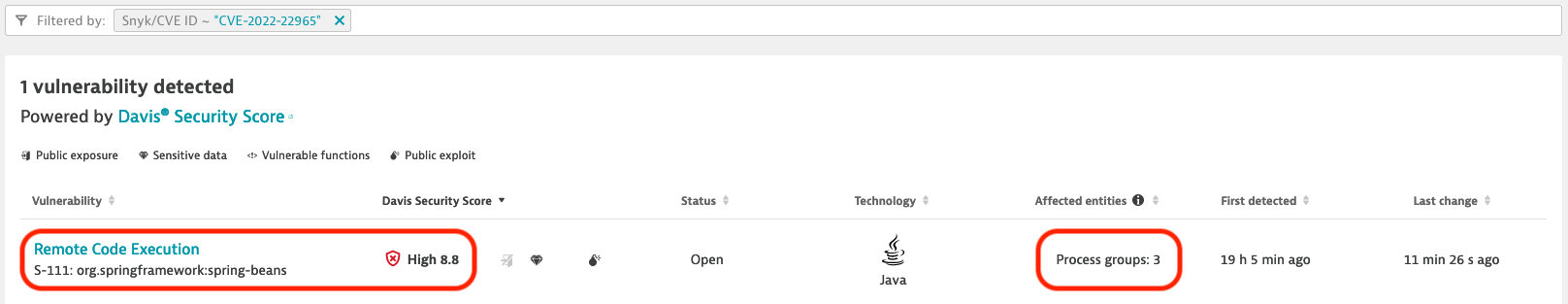
- Now, click on Remote Code Execution to show further details about this vulnerability.
- Here you can see all the details about this specific vulnerability:
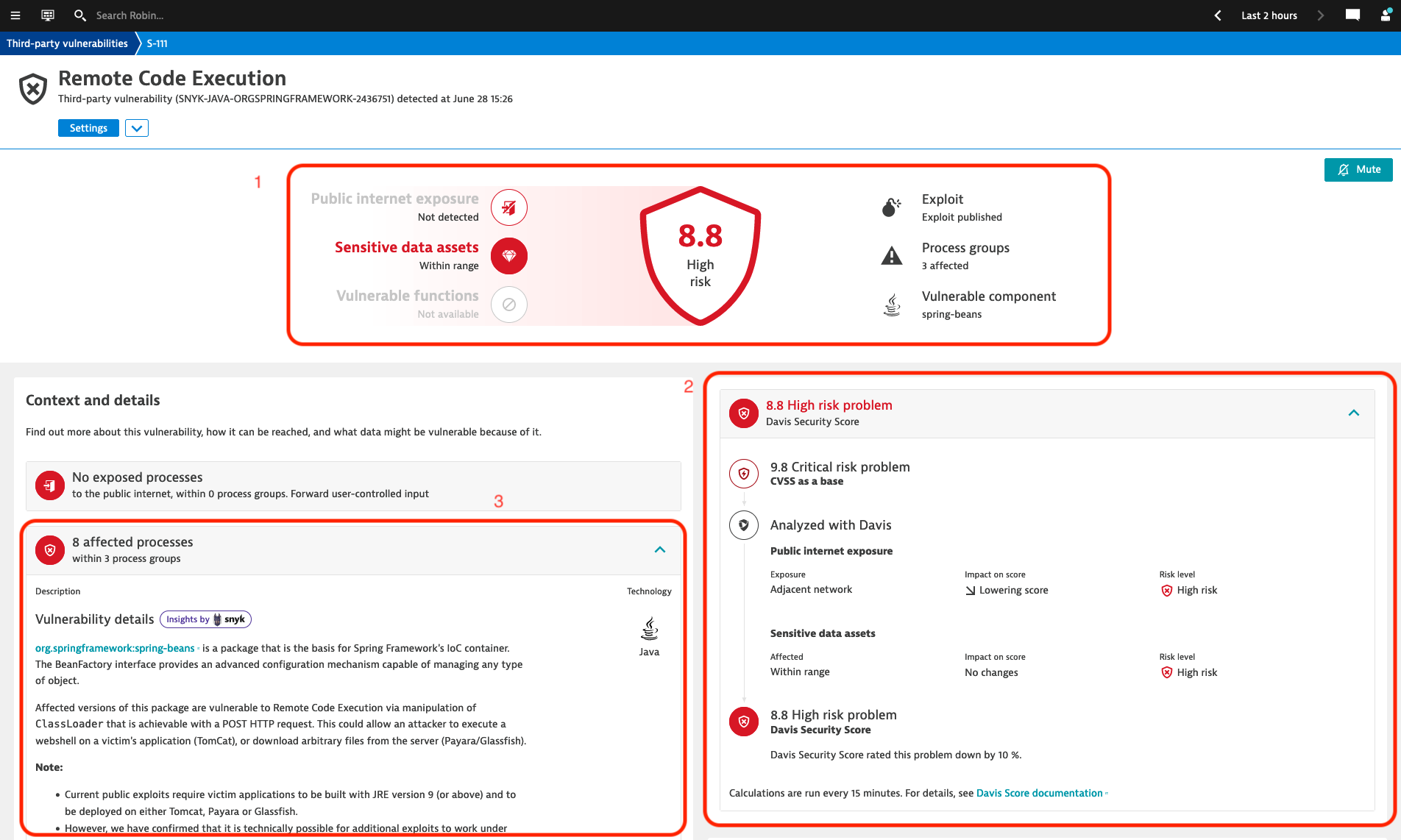
- At the top you can see the context information, it shows that no public internet exposure was detected, meaning that all requests to the affected processes are from the local network. However, the Sensitive data assets indicates that the there is a access to a database from at least one of the processes, meaning that some data could be at risk. Meanwhile on the right side, it is indicated that there is a public exploit available for this vulnerability, making it easier for potential attackers to exploit the vulnerability.
- Here you can see how the Davis Security Score was calculated. Its original CVSS is a 9.8, but now that Davis has factored in the contextual information, it has been lowered to 8.8. This is because, although reachability to Sensitive Data has been identified, there is no Public Internet Exposure as all requests come from Adjacent networks. This helps you prioritize the different vulnerabilities.
- Under context and details you can see that there are 8 processes in 3 process groups that are affected by the vulnerabily. A description of the vulnerability is also provides, for example it mentions that the current known exploits affect applications deployed on Tomcat, Payara or Glassfish using Java 9 or higher. Links to other resources, such as the National Vulnerability Database, OWASP and Snyk are also provided for further research.
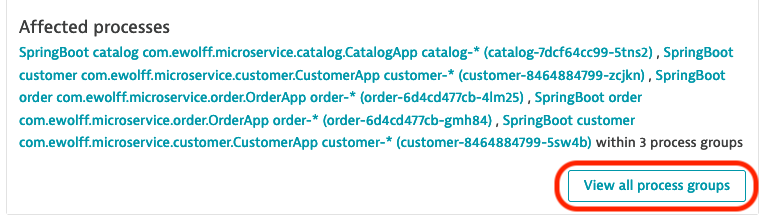
- By scrolling further down, you can see additional context informaion, like all affected processes, the affected container images and other related entities.
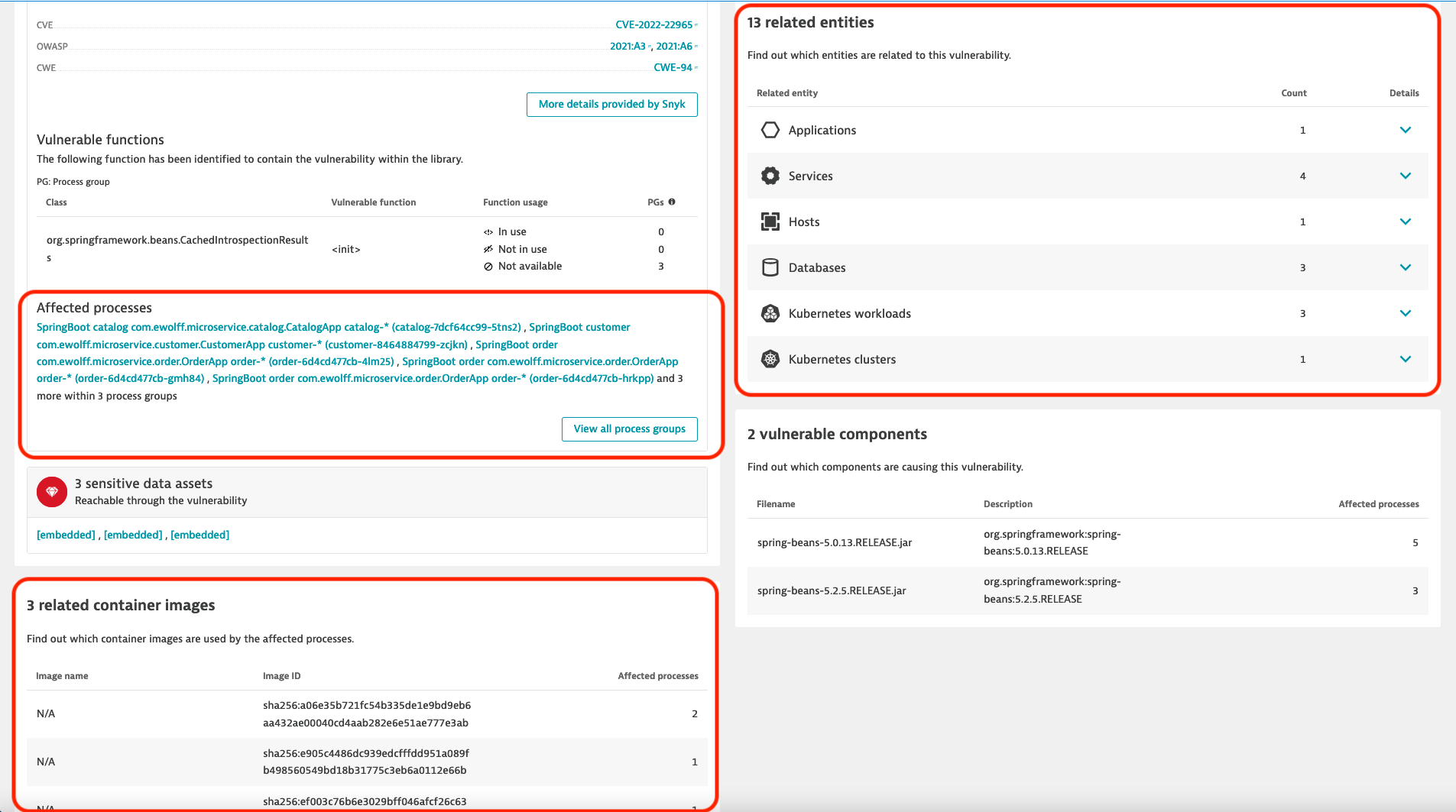
- Click on View all process groups.
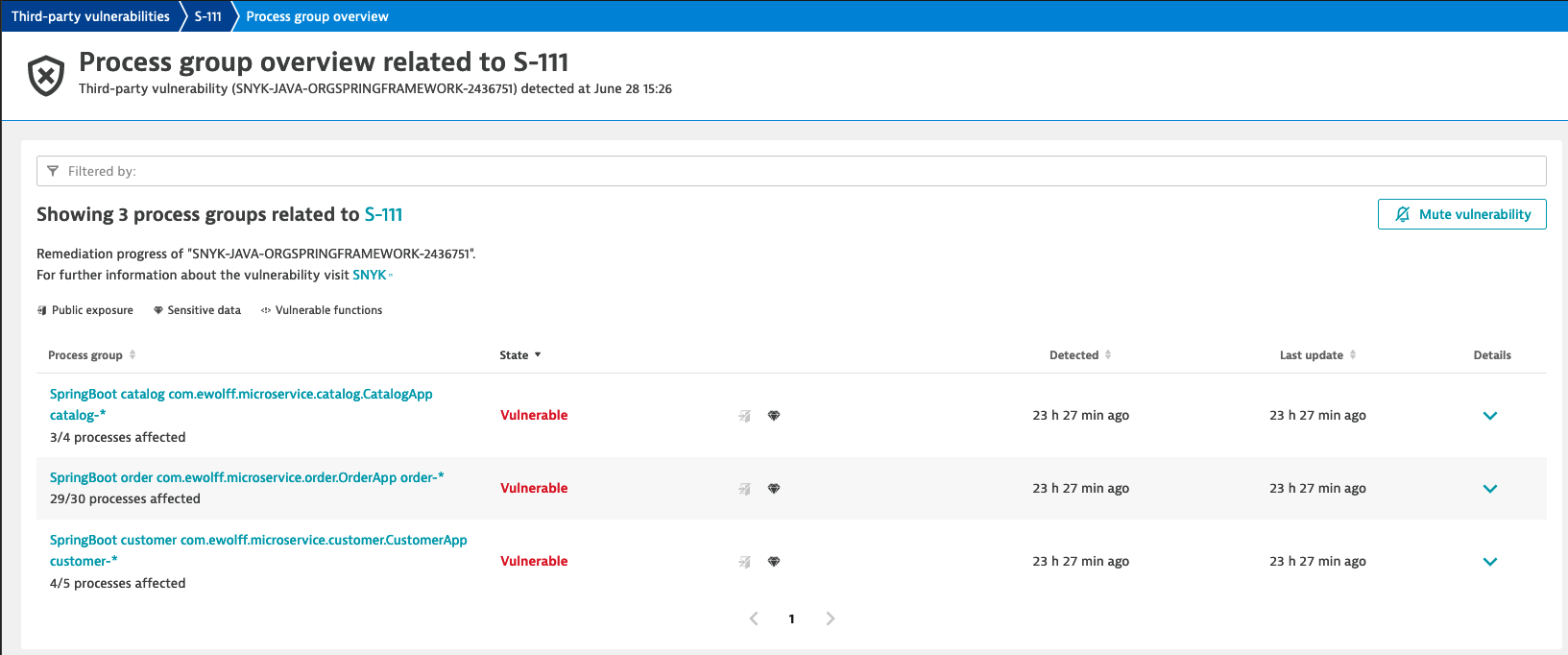
- This shows the list of all affected Process Groups. As we saw in the detail information about the vulnerability, currently the exploits are only known to work with Java 9 or newer and applications deployed in Tomcat, Payara or Glassfish. Since Dynatrace collects all these information at runtime, it is quite easy to see if the Process Groups match these criteria.
- First, click on the first Process Group to see the Process Group Details and expand the Properties and Tags section.
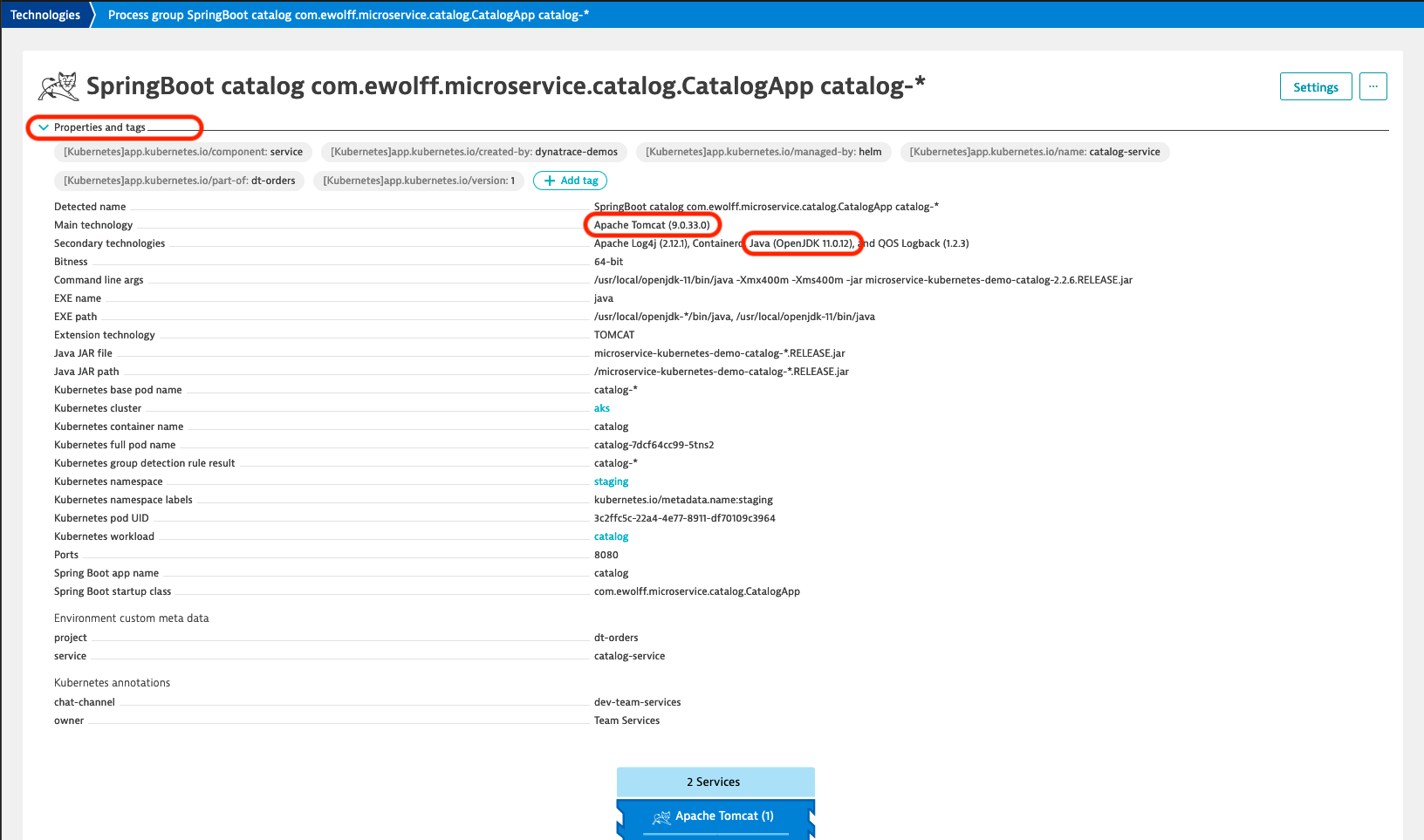
- As you can see in the properties, the application is deployed on Tomcat and is running on Java 11, meaning that it is affected by the spring4shell vulnerability.
- Click on View all process groups.